The MCP Security Crisis
Model Context Protocol is revolutionizing AI integration, but its transport-agnostic design introduces critical security vulnerabilities.
Security Standards
MCP deliberately leaves transport security to implementers, creating inconsistent and often vulnerable deployments across organisations. Every team reinvents the security wheel.
Real Security Incidents
CVE-2025-49596 (CVSS 9.4) demonstrates that MCP security risks are real and exploitable, not theoretical concerns. The threat landscape is evolving faster than security implementations can keep pace.
Enterprise Adoption Blocked
Organisations want the benefits of AI integration, but security teams reject MCP deployments without certified transport security. Business value is trapped behind security concerns.
Development Bottlenecks
Every team implements MCP security differently, creating maintenance nightmares and security review delays that can last for months. Innovation velocity suffers.
Immediate Security Vulnerabilities
- AI Agent Impersonation
- Context Injection Attacks
- Model Parameter Theft
Specific MCP Protocol Vulnerabilities
- Multi-Agent Communication Hijacking
- Man-in-the-Middle Protocol Attacks
- Context Poisoning at Scale
- Message Tampering & Replay Attacks
- Resource Access Privilege Escalation
Developer-Specific Problems
- Integration Nightmares
- Debugging Hell
- Compliance Violations
Enterprise-Scale Disasters
- AI Supply Chain Attacks
- Federated Learning Violations
The Cost of Inaction
Organizations that fail to secure their AI communication protocols face data breaches, regulatory violations, and compromised AI model integrity. The time to act is now.
TLS Implementation Security Flaws
As organisations scramble to secure MCP with TLS, they're walking into a trap. The same implementation flaws that plague 94% of web services are now exposing AI systems—and attackers are already exploiting them.
False Security Everywhere
- 78% of TLS-enabled systems accept weak cipher suites despite claiming to be secure
Legacy Protocol Risks
- 45% of enterprise applications still support deprecated TLS 1.0/1.1 protocols from 1999
Known Vulnerabilities
- 67% of TLS implementations are vulnerable to at least one documented attack vector
Configuration Chaos
- The average enterprise manages 23 different TLS configurations across their infrastructure
Common Implementation Attack Scenarios
Real-world attack scenarios that exploit the gap between TLS specifications and actual implementations

The Advantage of Starting Fresh
While the web remains shackled to legacy TLS implementations, MCP is our chance to build security correctly from the ground up. TLSMCP delivers the Gold Standard that TLS always promised but never achieved: Truly Secure AI Communications.
The Solution: TLSMCP Security
A Step by Step process for implementing TLS for MCP designed for the complexity of modern AI ecosystems and Model Context Protocol implementations.
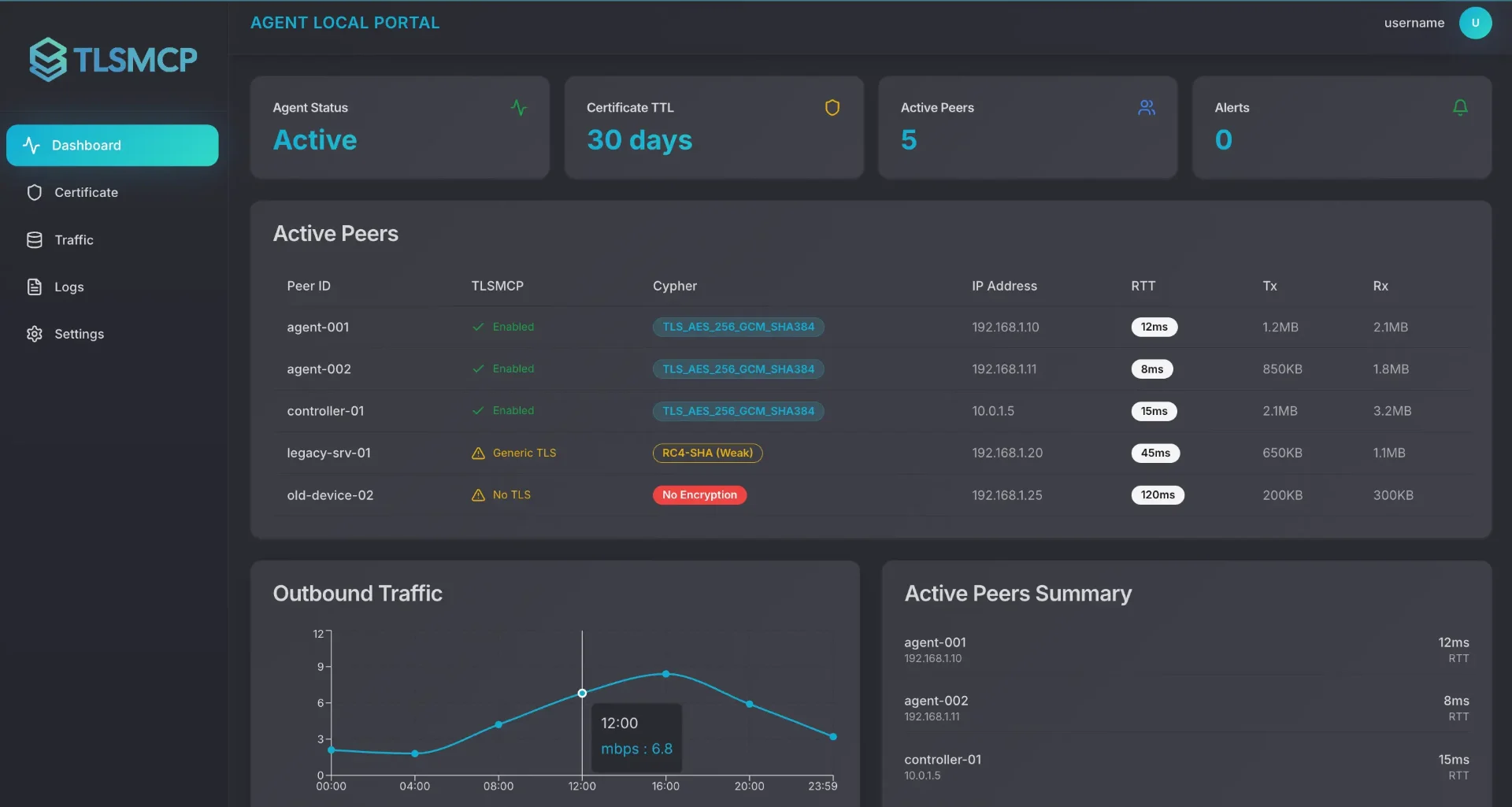
Certificate Lifecycle Management
Issue certificates for the Client and Server MCP entity and manage ongoing certificate rotation and revocation.
mTLS Handshake
Both sides authenticate before any data is exchanged. Client and server exchange certificates, verify identities, and establish a trusted channel, blocking unauthorised connections at the very first handshake.
Encrypted Channel
A TLS 1.3 tunnel is established - no downgrades, no weak cyphers, no compromises.
Real-time Monitoring
Intelligent traffic analysis identifies and blocks suspicious patterns in real-time. From DDoS attempts to data exfiltration, TLSMCP monitors every connection for anomalies—protecting your AI infrastructure at wire speed.
Our Mission
Securing the Future of AI Communication
We built TLSMCP because we witnessed firsthand how vulnerable AI systems become as they scale. Traditional cybersecurity tools weren't designed for the unique challenges of implementing TLS for MCP and AI communication protocols. Our mission is to provide the TLS for MCP security infrastructure that enables organizations to deploy AI safely, confidently, and at scale.
For Developers
We eliminate the complexity of securing AI communications, allowing developers to focus on innovation rather than security implementation. Our tools integrate seamlessly into existing workflows and provide clear, actionable insights.
For Enterprises
We provide the governance, compliance, and risk management tools that enterprises need to deploy AI systems responsibly. Our platform scales with your organization and adapts to evolving regulatory requirements.
Knowledge Hub
Deep insights into AI security, MCP, and TLS implementation. Stay informed with expert analysis and practical guidance.
No articles available yet.
Stay updated with the latest AI security insights. Learn more about our comprehensive approach to MCP security.
Frequently Asked Questions
Get answers to common questions about TLSMCP implementation and capabilities.
Join the Waiting List
Be among the first to experience enterprise-grade AI security. Get early access and exclusive updates on TLSMCP development.
